In Lab setup we had installed AD with DNS with basic configuration, now will go with advanced configuration. DNS is basically responsible for resolving name in to UP and vise versa in network and there has lots of changes in MS server from 2003, 2008 and 2012 server. Different concept added to newer server version operating system. Its always recommend that Install DNS with and on the same server with Active Directory.
The very interesting and deep drive question that why this need to be install with AD only, and thte answer would be because DNS provides an enterprise-level tool for organizing, managing, and locating resources in a network.
1.DNS Service will help to locate, find and proper response for Domain Controllers
Net Logon service use DNS server only to register of domain controllers in your DNS domain namespace
2.DNS servers configured on Windows Server 2003 and 2008 can use AD DS for storing,replicating and reply with proper response in zones.With AD Integrated DNS ,its have more advanced feature like replication, DNS updates, aging, scavenging and more are there.In case of non-integrated AD with DNS Server a single authoritative DNS server for a zone is designated as the primary source for particular zone and this server is responsible and act as owner to maintains the master copy of zone in a local file. With this model, the primary server for the zone represents a single fixed point of failure. If this server is not available, update requests from DNS clients response will be on hold and will get response in error.
In case on Integrated DNS with AD, DNS updates will be sending to other available AD-DNS Integrated server in process of replication.All DNS data is replicated to DNS Server and is updating a period of time, and in worst case if primary or any other server is failed or any issue other DNS Server will respond to that client query.
Integrated DNS is more stable and faster replication in comparison of Non-integrated option Because integrated replication processing is performed on a per-property basis, only relevant changes are propagated. Less data is used and submitted in updates for directory-stored zones.In model of non-integrated structure only primary DNS zones can be stored in the directory. A DNS server cannot store secondary zones in the directory. It must store them in standard text files and in case of AD-DNS integrated tructure the multi master replication model of AD DS removes the need for secondary zones when all zones are stored in AD for the DNS zone.
Below are the main record in DNS
Host (A) resource records: domain name to an IP address that is used by a computer.
Alias (CNAME) resource records: another primary or canonical name.When a server is used for more than one purpose. Like multiple webpages on single server, FTP.
Mail exchange (MX) resource records: in case of exchanges or forwards mail.
Pointer (PTR) resource records: IP to Host Name
SOA (start of authority) Declares the host that is authoritative for zone and as per best practise near by source of DNS information for the zone. Each zone having an SOA record.
Service location (SRV) resource records: specified list of DNS host computers that offer a specific type of service, such as Active Directory domain controllers.
IN our scenario, we have 2003 and 2012 DNS Server. let me draw image here to understand DNS concept better.That we can use on all setup :)
Here you can see two images as reference with small and multi DNS structure. in Small DNS Structure its very easy to understand that first Root DNS is acting as primary and having all DNS information. If first stop responding to client query some how due to UN-avoidable situation then as per best practise and the configuration as been done in the network or server the second DNS will start responding to client query.For attached pic if any question just text here
After configuration DNS with AD Services, the zone data automatically replicated to all available server in domain. As its explained that how and why DNS-AD Integrated is better and safe in comparison of non-integrated Infrastructure, another important aspect and feature for integrated is application directory partition.These are directories stored in AD which contains data that is replicated to certain DNS servers, By creating this, your DNS environment will be secure and robust.From this option you can limit the replication with specific 2 DNS servers, to enable this configuration part you have to enlist only those servers.
At the time of Active Directory Integrated zone, there will be two partition build automatically DomainDnsZOnes and ForestDnsZones.
Domain Zone partition will replicate and update the data toll running available domain controllers in the network and Forest will replicate and update the information to available running domain controller in the forest network.
set aging/scavenging for all zones concept:
Scanvenange Stale Resource Records:
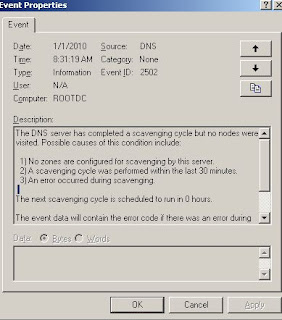
I tried to enable this in my lab setup but got this 2502 error.
and Microsoft recommend As per Microsoft: "This behavior occurs if you try to manually scavenge a DNS zone that supports dynamic updates immediately after you enable scavenging. You cannot scavenge the zone until the date and the time in the The zone can be scavenged after box is reached. If you try to manually scavenge the records before this date and time, the event ID 2502 message is logged. To work around this behavior, we recommend that you wait until the date and time that is defined in the The zone can be scavenged after box is reached before you start scavenging"
Basic commands which admins are using frequently
nslookup
ipconfig /flushdns
ipconig /registerdns
ipconfig/displaydns
Now will go through with DNS properties tab and there use for environment.
From here you can set the IP addresses that should handle DNS requests and responses
In Forwarder Tab, Servers are designated to received req or query to forward. Forwarders use DNS communication methods to resolve queries and req to send responses back to other DNS servers You can add the DNS server IP which will act as forwarder.Means If user from different domain want a response from trusted other domain so you can add other domain name here.In this tab there is another option is Do not use recursion for this domain which means if your DNS server failed or you dont want to make more traffic load to response the query, so you can check this box and it will stop resolving queries. Let me explain you with another simple example where if you configured server using conditional forwarding option to resolve queries and request for another domain or trusted domain name in internal zone, and if a response to client req failed, you dont want DNS to continue to search other DNS servers of name resolution.
If this option is enabled then DNS Server will respond the client query from its own database only, it will not forward or check with another available or additional DNS servers.As best practise this option should be enabled (Due to security and audit policy in example of trusted domain infrastructure)Disable Recursion status ca be check by running command : Dnscmd /Info /SecureResponses
In 2000 server MS have lots of known issue in DNS cache part, Secure cache against pollution option enable to prevent wrong or malfuntction entries from a serevr to outside domain. if this is allowed to cache, then ther will be name resoltion issue. ipconfig /displaydns command shows the cache entry on the server.
BIND Seondaries: i disabled this option and i found that it impact on zone tranfer. means if i unselect this the zone tranfer was fast and if select then it was very slow in regard of update zone data to another DNS servers.
Reg Setting will be HKLM\SYSTEM\CurrentControlSet\Services\DNS\Parameters with REG_DWORD(Data Type) with Default Value of 1.
Fail On Load If Bad Zone Data:by enabling this option DNS server will fail when there is a bad or malfunation data on zoen,Generally, this is a setting we should not enable
Enable Round Robin:Its a well known term for most of technology, where load balancing comes in feature.To avoid load on one DNS server this terms help to enable load balance. If one server having high traffic for cleint req to ti will move the req to another available DNS server.
Enable Netmask Ordering:If you have computers that have more than one NIC (aka multihomed), this setting allows your DNS server to answer with the address that is on the same subnet of the client.
Secure Cache Against Pollution:If enabled, the DNS server will prevent the caching of resource records that were not answers for the originally issued query.MS Article have explained very well with comparison with other Server version OS(https://support.microsoft.com/en-us/kb/241352)
Root Hints:its shows a list of all DNS servers at the root of the Internet and is used for recursive name resolution.
Debug Logging:It recommended to enable logging that will capture the packet sent and received by DNS servers as a log file. you can capture the DNS traffic as per your requirement. which help to troubleshoot and keep an eye on the DNS data. Event Logging: by default this will log all events, and you can customized it.
Monitoring: A good tool to check DNS staus, as status it will show as pass or fail. Even you can schedule this test as per your requirement.
There are other lots of option in DNS server for configuration on large scale, will be explore and share with you very soon.
The very interesting and deep drive question that why this need to be install with AD only, and thte answer would be because DNS provides an enterprise-level tool for organizing, managing, and locating resources in a network.
1.DNS Service will help to locate, find and proper response for Domain Controllers
Net Logon service use DNS server only to register of domain controllers in your DNS domain namespace
2.DNS servers configured on Windows Server 2003 and 2008 can use AD DS for storing,replicating and reply with proper response in zones.With AD Integrated DNS ,its have more advanced feature like replication, DNS updates, aging, scavenging and more are there.In case of non-integrated AD with DNS Server a single authoritative DNS server for a zone is designated as the primary source for particular zone and this server is responsible and act as owner to maintains the master copy of zone in a local file. With this model, the primary server for the zone represents a single fixed point of failure. If this server is not available, update requests from DNS clients response will be on hold and will get response in error.
In case on Integrated DNS with AD, DNS updates will be sending to other available AD-DNS Integrated server in process of replication.All DNS data is replicated to DNS Server and is updating a period of time, and in worst case if primary or any other server is failed or any issue other DNS Server will respond to that client query.
Integrated DNS is more stable and faster replication in comparison of Non-integrated option Because integrated replication processing is performed on a per-property basis, only relevant changes are propagated. Less data is used and submitted in updates for directory-stored zones.In model of non-integrated structure only primary DNS zones can be stored in the directory. A DNS server cannot store secondary zones in the directory. It must store them in standard text files and in case of AD-DNS integrated tructure the multi master replication model of AD DS removes the need for secondary zones when all zones are stored in AD for the DNS zone.
Below are the main record in DNS
Host (A) resource records: domain name to an IP address that is used by a computer.
Alias (CNAME) resource records: another primary or canonical name.When a server is used for more than one purpose. Like multiple webpages on single server, FTP.
Mail exchange (MX) resource records: in case of exchanges or forwards mail.
Pointer (PTR) resource records: IP to Host Name
SOA (start of authority) Declares the host that is authoritative for zone and as per best practise near by source of DNS information for the zone. Each zone having an SOA record.
Service location (SRV) resource records: specified list of DNS host computers that offer a specific type of service, such as Active Directory domain controllers.
IN our scenario, we have 2003 and 2012 DNS Server. let me draw image here to understand DNS concept better.That we can use on all setup :)
Here you can see two images as reference with small and multi DNS structure. in Small DNS Structure its very easy to understand that first Root DNS is acting as primary and having all DNS information. If first stop responding to client query some how due to UN-avoidable situation then as per best practise and the configuration as been done in the network or server the second DNS will start responding to client query.For attached pic if any question just text here
After configuration DNS with AD Services, the zone data automatically replicated to all available server in domain. As its explained that how and why DNS-AD Integrated is better and safe in comparison of non-integrated Infrastructure, another important aspect and feature for integrated is application directory partition.These are directories stored in AD which contains data that is replicated to certain DNS servers, By creating this, your DNS environment will be secure and robust.From this option you can limit the replication with specific 2 DNS servers, to enable this configuration part you have to enlist only those servers.
At the time of Active Directory Integrated zone, there will be two partition build automatically DomainDnsZOnes and ForestDnsZones.
Domain Zone partition will replicate and update the data toll running available domain controllers in the network and Forest will replicate and update the information to available running domain controller in the forest network.
Scanvenange Stale Resource Records:
I tried to enable this in my lab setup but got this 2502 error.
and Microsoft recommend As per Microsoft: "This behavior occurs if you try to manually scavenge a DNS zone that supports dynamic updates immediately after you enable scavenging. You cannot scavenge the zone until the date and the time in the The zone can be scavenged after box is reached. If you try to manually scavenge the records before this date and time, the event ID 2502 message is logged. To work around this behavior, we recommend that you wait until the date and time that is defined in the The zone can be scavenged after box is reached before you start scavenging"
Basic commands which admins are using frequently
nslookup
ipconfig /flushdns
ipconig /registerdns
ipconfig/displaydns
Now will go through with DNS properties tab and there use for environment.
From here you can set the IP addresses that should handle DNS requests and responses
In Forwarder Tab, Servers are designated to received req or query to forward. Forwarders use DNS communication methods to resolve queries and req to send responses back to other DNS servers You can add the DNS server IP which will act as forwarder.Means If user from different domain want a response from trusted other domain so you can add other domain name here.In this tab there is another option is Do not use recursion for this domain which means if your DNS server failed or you dont want to make more traffic load to response the query, so you can check this box and it will stop resolving queries. Let me explain you with another simple example where if you configured server using conditional forwarding option to resolve queries and request for another domain or trusted domain name in internal zone, and if a response to client req failed, you dont want DNS to continue to search other DNS servers of name resolution.
If this option is enabled then DNS Server will respond the client query from its own database only, it will not forward or check with another available or additional DNS servers.As best practise this option should be enabled (Due to security and audit policy in example of trusted domain infrastructure)Disable Recursion status ca be check by running command : Dnscmd /Info /SecureResponses
In 2000 server MS have lots of known issue in DNS cache part, Secure cache against pollution option enable to prevent wrong or malfuntction entries from a serevr to outside domain. if this is allowed to cache, then ther will be name resoltion issue. ipconfig /displaydns command shows the cache entry on the server.
BIND Seondaries: i disabled this option and i found that it impact on zone tranfer. means if i unselect this the zone tranfer was fast and if select then it was very slow in regard of update zone data to another DNS servers.
Reg Setting will be HKLM\SYSTEM\CurrentControlSet\Services\DNS\Parameters with REG_DWORD(Data Type) with Default Value of 1.
Fail On Load If Bad Zone Data:by enabling this option DNS server will fail when there is a bad or malfunation data on zoen,Generally, this is a setting we should not enable
Enable Round Robin:Its a well known term for most of technology, where load balancing comes in feature.To avoid load on one DNS server this terms help to enable load balance. If one server having high traffic for cleint req to ti will move the req to another available DNS server.
Enable Netmask Ordering:If you have computers that have more than one NIC (aka multihomed), this setting allows your DNS server to answer with the address that is on the same subnet of the client.
Secure Cache Against Pollution:If enabled, the DNS server will prevent the caching of resource records that were not answers for the originally issued query.MS Article have explained very well with comparison with other Server version OS(https://support.microsoft.com/en-us/kb/241352)
Root Hints:its shows a list of all DNS servers at the root of the Internet and is used for recursive name resolution.
Debug Logging:It recommended to enable logging that will capture the packet sent and received by DNS servers as a log file. you can capture the DNS traffic as per your requirement. which help to troubleshoot and keep an eye on the DNS data. Event Logging: by default this will log all events, and you can customized it.
Monitoring: A good tool to check DNS staus, as status it will show as pass or fail. Even you can schedule this test as per your requirement.
There are other lots of option in DNS server for configuration on large scale, will be explore and share with you very soon.











DNS advanced configuration varies slightly across Microsoft Server versions, focusing on role-based installation and zone settings. Newer versions like Server hostbet offer improved DNSSEC, conditional forwarding, and better GUI support.
ReplyDelete